Looking around today’s world, we notice how our everyday life relies on technology more than ever. The advantages of these developments include almost instantaneous access to information on the Internet and the contemporary comforts offered by smart home automation systems and ideas such as the Internet of Things.
It might be difficult to accept that possible risks hide behind every gadget and platform when technology has brought about so much good. However, cyber security dangers posed by contemporary electronics are a serious concern, despite society’s optimistic view of these advancements. An increasing amount of cybercrime exposes the weaknesses in the products and services we’ve become accustomed to using. This issue compels us to consider the definition of cyber security, its importance, and the necessary knowledge.
Hadooken Malware: A NewThreat to WebLogic Servers
Cybersecurity experts have uncovered a new Linux malware outbreak, ” Hadooken, especially targeting Oracle WebLogic servers. The Tsunami backdoor and a crypto miner are the final products of this multi-stage attack chain used by this sophisticated virus, which puts businesses who depend on WebLogic for their vital applications in danger. A new Linux worm known as “Hadooken,” which starts a crypto miner and a tool for distributed denial-of-service (DDoS) assaults, is being used by hackers to infect Oracle WebLogic servers. On Windows systems, the acquired access could potentially be used to carry out ransomware attacks.
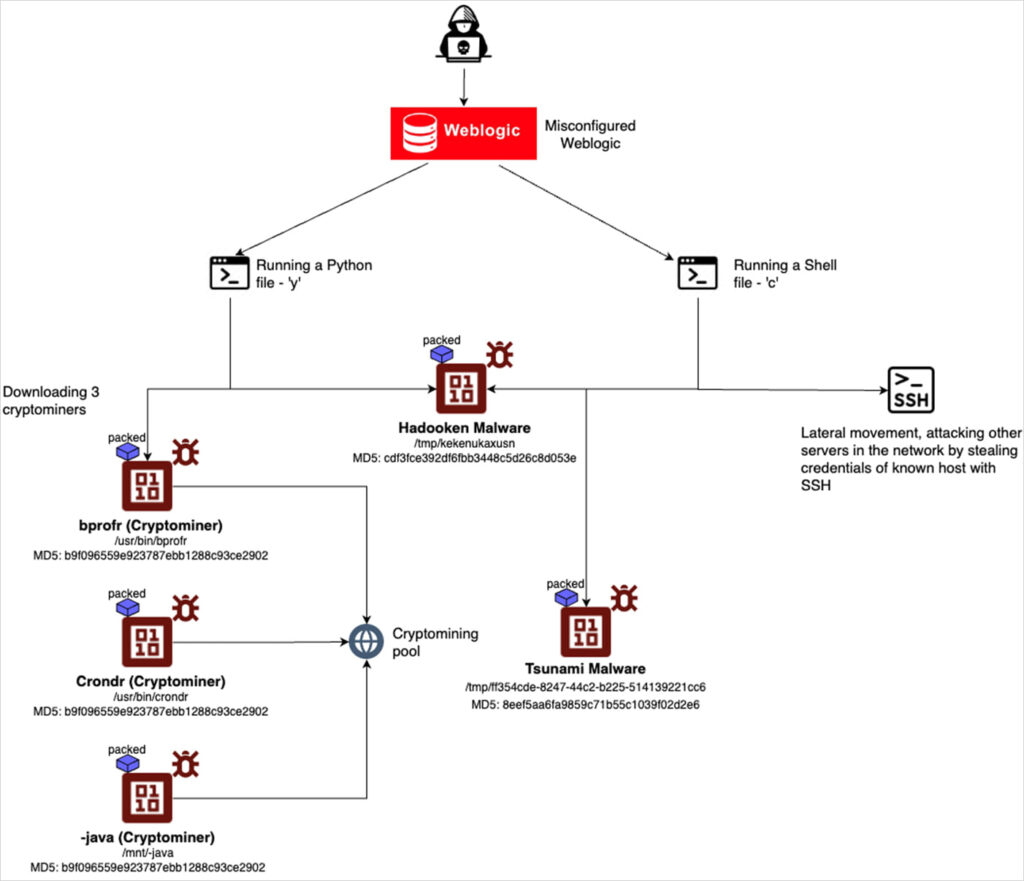
Such an attempt was seen by researchers at a cyber security business on a honeypot, which the threat actor had compromised because of shoddy credentials. To develop, implement, and overseeing expansive, dispersed applications, Oracle WebLogic Server is an enterprise-class Java EE application server. The product is frequently utilized by government agencies, public services, e-commerce, banking, and financial services. Because WebLogic is widely used in business-critical environments with abundant processing power, which are perfect for DDoS and cryptocurrency mining, attackers often target these environments.
Hadooken hitting hard
After breaking into a system and gaining enough access, the attackers download two scripts: one in Python called “y” and another in a shell called “c.” The researchers claim that although Hadooken is dropped by both scripts, the shell code also searches different folders for SSH information and then utilizes that information to launch attacks against known servers.
Furthermore, to disperse Hadooken throughout the network, ‘c’ travels laterally. Hadooken then drops and runs the Tsunami malware together with a cryptominer, and creates many cron jobs with random payload execution frequencies and names. A Linux DDoS botnet virus called Tsunami uses brute-force assaults on weak passwords to infect SSH servers that are susceptible to compromise. Tsunami has already been used by attackers to initiate DDoS assaults and acquire remote control over infected systems; it has since been spotted being used in conjunction with Monero miners once more.

Researchers in cyber security draw attention to Hadooken’s habit of hiding harmful services behind the ‘-bash’ or ‘-java’ suffix to imitate genuine processes and blend in with everyday activities.
After this procedure is finished, system logs are erased and cleaned to conceal any evidence of malicious activity, which makes forensic investigation and discovery more difficult. Links to the RHOMBUS and NoEscape ransomware families were found through static analysis of the Hadooken binary; however, no ransomware modules were used in the assaults that were detected. The researchers hypothesize that, under some circumstances, such as when the operators do manual inspections, the server access may be exploited to spread ransomware. Another possibility is that the feature will be added in a later version.
Furthermore, the researchers found a PowerShell script that downloaded the Maalox ransomware for Windows on one of the servers hosting Hadooken (89.185.85[.]102). More than 230,000 Weblogic servers are accessible on the public internet, according to the researchers’ results via their use of the Shodan search engine for internet-connected devices.
Massive Security Vulnerabilities in Major Protocols
Hadooken first obtains access via brute-forcing weak administrative passwords or by taking advantage of known flaws in WebLogic servers. Once inside, it downloads and launches its malicious payload by executing several scripts. Because of its sophisticated use of shell scripts and Python, the virus can function in a variety of Linux environments.
It indicates that Hadooken’s main goal is to mine cryptocurrencies illegally using the victim’s computer power to make money for the attackers. Nonetheless, the existence of the Tsunami backdoor gives rise to other worries. A tsunami is a multipurpose virus that is well-known for its capacity to establish a stronghold on infiltrated computers, allowing attackers to carry out other malicious operations, such as data exfiltration or lateral network movement.
There are also concerns about lateral movement capabilities displayed by the Hadooken virus. It may be able to propagate to other computers on the network of the company by aggressively searching for SSH credentials kept on the compromised server. Furthermore, the virus tries to hide its presence by deleting system records, which complicates detection and incident response.
Detection and Mitigation
Cloud-native developers may identify and avoid misconfigurations by using a number of tools and best practices. These technologies usually concentrate on cloud service setups, runtime environments, Kubernetes, container security, infrastructure as code (IaC), and so on.
- Cloud Security Posture Management (CSPM) Tools: CSPM tools monitor cloud setups for possible security threats, misconfigurations, or compliance lapses across a range of cloud services (e.g., AWS, Azure, GCP).
- Kubernetes Security and Configuration Tools: Kubernetes security and configuration tools are available to check for any misconfigurations in clusters, pods, and deployments. Kubernetes clusters are a crucial component of cloud-native designs.
- Container Security Tools: Since containers are the foundation of cloud-native development, it is important to review their settings, including Docker files and container images, for security vulnerabilities.
- Runtime Security Tools: These instruments keep an eye on cloud-native services and apps that are currently in use to instantly identify abnormalities, incorrect setups, or questionable activity.
Execution
- Command and Scripting Interpreter – Unix Shell: The use of shell script (`c`) for malicious execution.
- Command and Scripting Interpreter – Python: The use of Python script (`y`) for malicious execution.
- Command and Scripting Interpreter – PowerShell: PowerShell script `b.ps1` used to distribute malware (Mallox ransomware).
Defense Evasion
- Masquerading–Task or Service: Use of known names such as -java, -bash.
- Obfuscated Files or Information: Use of base64-encoded payloads to avoid detection.
- Indicator Removal on Host: Deleting logs after executing malicious activities.

It is highly recommended that enterprises using WebLogic servers take prompt steps to safeguard themselves against this new danger.
Key recommendations include:
- Install Security Patches: To reduce known vulnerabilities, make sure all WebLogic servers have the most recent security patches installed.
- Enforce Strong Passwords: Give each administrative account a complicated, one-of-a-kind password, and think about using multi-factor authentication.
- Track Network Activity: To discover and stop questionable activity, use effective intrusion detection and network monitoring technologies.
- Frequent Backups: To facilitate recovery in the event of a successful attack, keep regular backups of your most important data.



